I have one or two allegedly white hat friends and enjoy stories of lore and legend regarding their chivilarous and well contained sporting activites. However when it comes to professional cyber crime, I feel my Tokyo life is somewhat sheltered from the darker forces that glide through the veins and fibre cables of the internet (this may be in part to being a non-windows user), so I was rather intreiged by one of this morning’s comments on my blog:
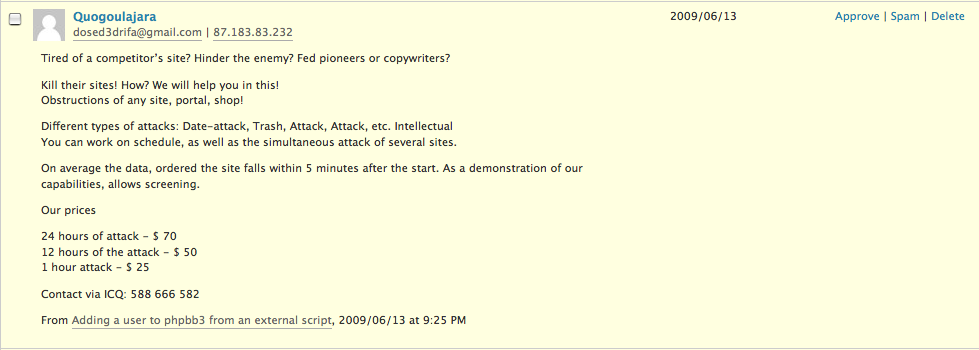
Tired of a competitor’s site? Hinder the enemy? Fed pioneers or copywriters?
Kill their sites! How? We will help you in this!
Obstructions of any site, portal, shop!Different types of attacks: Date-attack, Trash, Attack, Attack, etc. Intellectual
You can work on schedule, as well as the simultaneous attack of several sites.On average the data, ordered the site falls within 5 minutes after the start. As a demonstration of our capabilities, allows screening.
Our prices
24 hours of attack – $ 70
12 hours of the attack – $ 50
1 hour attack – $ 25
I note that perhaps a copywriter/proof reader might benefit this particular ‘Cyber Mercenary’, or perhaps there is a subtle difference in the third line between ‘Attack’ and ‘Attack’ to which I am not yet attuned.
Oh, and here’s an example attack that was “clearly ordered by someone”.
Surfed onto your blog, I enjoyed the post. This is a very solid example of what is all too real and what many would rather didn’t exist (and what some prefer to believe does not exist), today in the wilds of the Internet. Many would rather chase the dragon’s tail of compliance which is, of course, necessary but not equal to ensuring security in and of itself. There are philosophical and practical arguments abounding on that and I won’t clutter your blog with them. Good stuff! I enjoyed it.
Best,
Will Gragido